Training

Core Courses
Wireless Operations Course - WiOC

Duration: 3 Weeks
This is an introductory course in which students will learn to operationalize the cyberspace domain in support of GFC priorities.
Graduates of WiOC earn the title of Tactical Cyber Operator I (TCO I). They can design, build, and secure packet-switched networks, and conduct wireless find/fix operations. Students will learn to operationalize technical tasks in a way that is reliable and repeatable.
Key Points of Instruction:
-
Networking
-
Offensive Cyberspace Operations Planning & Rehearsals
-
Wireless Survey techniques & tools
-
Post Processing & Analysis
-
WPA/2 Handshake Capture
-
802.11 Protocol and RF Theory
-
Single Board Computer (SBC) Operations
Wireless Bridging Course - WBC

Duration: 4 Weeks
This is an intermediate course in which students will learn to bridge network access to remote cyber partners through proximal access vectors.
Graduates of WBC earn the title of Tactical Cyber Operator II (TCO II). They can conduct active wireless operations, tunneling, and bridging network access to Remote Cyber Operators with a high degree of technical and tactical tradecraft.
Key Points of Instruction:
-
WIFI attacks (capture/crack)
-
Expeditionary Platform hardening
-
Advanced tunneling techniques
-
Pivoting techniques & traffic routing
-
Tunneling tools
-
VPN client/server management
-
Captive Portal bypass
-
Network discovery & digital tradecraft
Tactical Cyber Course - TCC

Duration: 8 Weeks
This is an advanced course in which students will learn GOTS and Open-Source network exploitation through unilateral and surrogate enabled cyberspace operations.
Graduates of TCC earn the title of Tactical Cyber Operator III (TCO III) and are subject matter experts who can plan, execute, and advise commanders on all phases of Tactical Cyber Operations.
Key Points of Instruction:
-
Python programming
-
Advanced WIFI exploitation techniques
-
Network reconnaissance
-
Open-Source exploitation
-
GOTS exploitation/Simulated Tool Suite
-
Surrogate-enabled exploitation
-
Electronics & Soldering
-
Living off the land techniques
-
Embedded systems architecture & Exploitation
-
Cross compilation, toolchains, & target emulation

A full course catalogue and course outlines are available upon request.



UEI: Y226JNYJ74F9
Cage: 9G6Z6
COMPANY

Train as you fight
We offer practical, real-world training and exercise support to clients in the DoD and the private sector. Our priority is to equip clients with the latest Tactics, Techniques, and Procedures in the rapidly evolving fields of cyber and communications, helping them stay ahead of the curve.
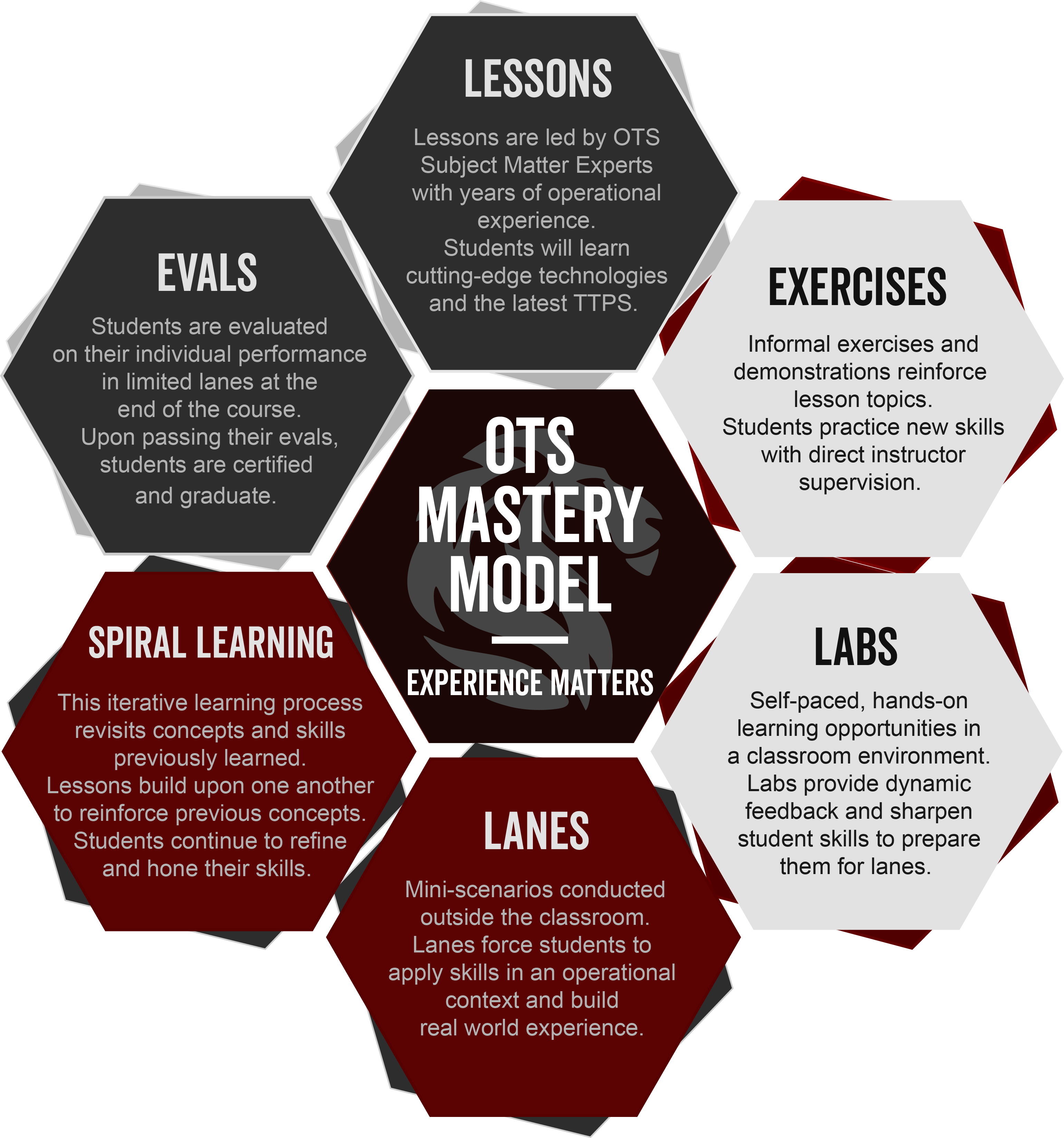
Our OTS Mastery Model blends classroom instruction, lab exercises, and field training, emphasizing hands-on, practical experience. Our team is committed to providing the highest level of expertise and support to clients, enabling them to tackle any challenges that come their way.